The Elevate Cyber Security Toolkit is a collection of key documents that schools can use to elevate their cyber security. It has been designed to meet both the DfE's Cyber Security Standards for Schools Colleges and guidance the NCSC developed following our joint cyber security audits with them.
DfE Aligned Cyber Security Audit and Checks
Cyber Security Audit
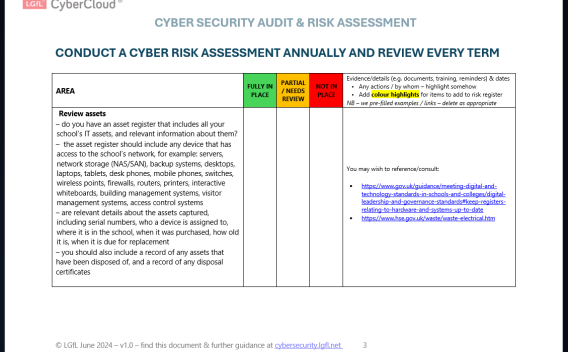
The DfE have updated their Cyber Security Standards for Schools and Colleges. There is now a requirement to conduct cyber security risk assessments annually. This document is designed to help schools complete such an assessment.
Cyber Security Checks
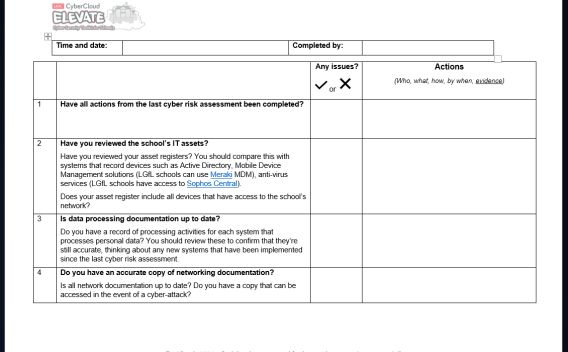
The DfE have updated their Cyber Security Standards for Schools and Colleges. As well as the requirement to conduct cyber security risk assessments annually there is also a need to complete termly checks. This document is designed to help schools complete these.
Key Cyber Security Governance Documents
Cyber Security Policy Template
This cyber security policy should complement schools' existing social media and acceptable use policies. The policy outlines the school’s guidelines and security provisions that are there to protect its systems, services, and data in the event of a cyberattack.

Incident Response Plan
If your school is unfortunate enough to fall victim to a ransomware attack, or any other kind of unforeseen outage it needs a plan for how to recover. This Incident Response Plan can be used as a starting point for planning how you would recover.

Risk Reporting Template
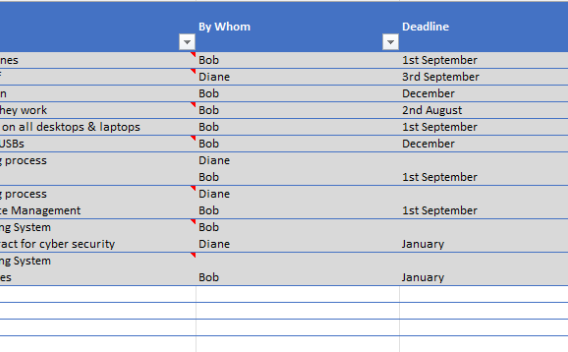
As the DfE have identified a need for governors to receive cyber security training it is there will be increasing interested in the way that schools manage their cyber security risks. It is important for schools to have a clear and concise way to report on their cyber security posture. This template can be used in conjunction with the Risk Register to provide a comprehensive overview of your school's cyber security risks and the measures you're taking to control them.

Example Registers
Example Risk Register
This example risk register can be used to Assess, Evaluate, Prioritise and Manage cyber security risks. It is a great tool to help support how schools report to governors on how they are proactively managing risks and improving their cyber security.
Example Asset Register
It sounds obvious, but it’s impossible to be secure if you don’t know what you have. This asset register can be used as a starting point to inventory the equipment used in your school.
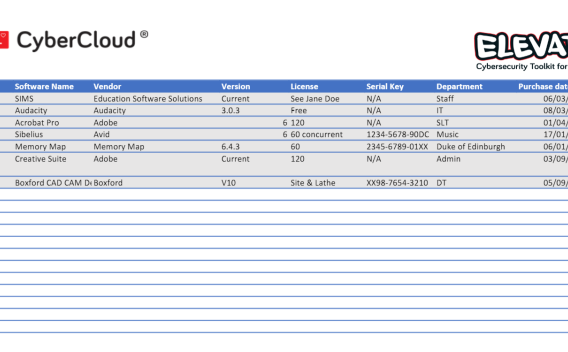
Example Software Register
In the same way that you can’t be secure if you don’t know what equipment you have, you also need to know which software and systems hold confidential information. This software register can be used to record which software/systems you have and whether they hold confidential information. It can be used to complement the Incident Response Plan to prioritise the recovery of services.